| Version 2 (modified by aaraujo, 7 years ago) (diff) |
|---|
CIA
https://protonmail.com/blog/cia-wikileaks-encryption/
advanced malwares enable the CIA to record actions such as keystrokes on a mobile device, allowing them to conduct surveillance without breaking encryption. Through this technique, US intelligence agencies can gain access to data before they have been encrypted. What the CIA files dumped by Wikileaks do reveal however, is a significant shift in strategy since the last disclosure of this kind was made by Edward Snowden in 2013. .
the varied leaked files are tied together by a common thread – an almost singular focus on producing malware to attack end-user devices
How is it different from the Snowden leaks: Snowden leaks exposed the NSA and its techniques of blanket surveillance on citizens and governments around the world. Vault7, on the other hand, exposes the CIA and what technologies it uses in cyber warfare against foreign governments as well as against targeted individuals.
Hive is a multi-platform CIA malware suite that can be specifically utilized against states. “The project provides customizable implants for Windows, Solaris, MikroTik? (used in internet routers) and Linux platforms and a Listening Post (LP)/Command and Control (C2) infrastructure to communicate with these implants.”
Development Tradecraft DOs and DON'Ts
Guía de cosas que se deben hacer y no hacer en el desarrollo de herramientas de vigilancia!!! : how its malware should be hidden when deployed to avoid any fingerprints leading back to the US or the agency
HIVE
https://wikileaks.org/ciav7p1/#HIVE
Why is this critical (https://protonmail.com/blog/cia-wikileaks-encryption/)?
While we are still mapping the dangers of such findings and capabilities, some conclusions are clear.
- The CIA can frame other governments
By using Hive and zero days, the US can wage a cyber attack against a nation state while purposefully leaving behind a trace that leads to another state. As governments around the world migrate their infrastructure control to cyber space – any cyber attack can have a devastating effect if targeted against hospitals, power plants or telecommunications providers.
Guía de desarrollador de HIVE
Hive is a software implant designed with “Ring 2” operations in mind. It has two primary functions: beacon and interactive shell. By design, both are limited in features with the purpose of providing an initial foothold for the deployment of other full featured tools.
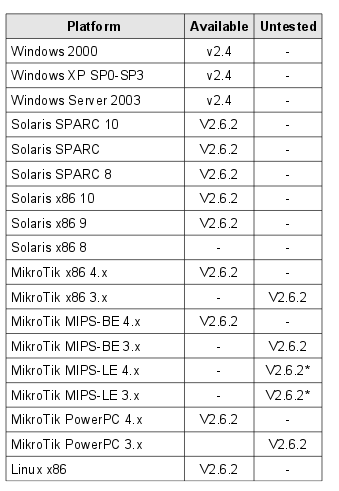
Hive provides implants for the following target operating systems and processor architectures.
Attachments (2)
- platform.png (34.6 KB) - added by aaraujo 7 years ago.
- hive.png (38.4 KB) - added by aaraujo 7 years ago.
Download all attachments as: .zip